Finding OWE in the RSNE
In this post, I cover analyzing the 802.11 RSNE information element to determine if a WiFi network is using OWE.
Table of Contents
Wi-Fi Alliance
In 2018, the Wi-Fi Alliance (WFA) introduced a “Certified” Enhanced Open program. Wi-Fi vendors participating in this program will be able to provide users (with compatible devices) an option to encrypt their Wi-Fi network connection while not requiring a password1.
Without Enhanced Open, wireless devices on an Open Network do not have an encrypted Wi-Fi connection (no encryption and no authentication). This makes programs like Enhanced Open important because a traditional Open network is not encrypted at Layer 22. This means Open network traffic is vulnerable to passive sniffing attacks.
-
If the coffee shop3 has an Open Wi-Fi network, an attacker could use traffic sniffing or other similar methods to capture and decrypt your Wi-Fi traffic. This is inexpensive and easy to perform.
-
One common misunderstanding is what if the coffee shop uses a password (PSK)? Is that secure?
- The PSK is used like a key to encrypt Wi-Fi traffic. One would simply need to ask the barista (or usually simply look on the wall, or other very similar tactics) what the Wi-Fi password is, and then use that password like a key to decrypt the Wi-Fi traffic.
- A Wi-Fi network secured with a PSK is only as secure as the knowledge of that PSK. This is like letting the public know the password to a Fortune 100 company social media account; only trusted folks should know that password! Once a network that uses a single PSK for authentication has a publicly known PSK, it’s encryption should be considered compromised.
Thankfully upper-layer security solutions4 are now pervasively used to provide a layered security approach for data. It goes without saying that the implementation of upper-layer security solutions is still important. Poor or wrong implementation is a security risk. And over time security solutions are compromised (see WEP for a classic example). A secure network will have many layers of security to prevent abuse over time.
Enhanced Open provides an encryption method called Opportunistic Wireless Encryption (OWE) to combat some of the security risks that Open networks present1.
OWE
Opportunistic Wireless Encryption (OWE) is an encryption standard for open Wi-Fi networks. This is what Enhanced Open uses and is based on the Internet Engineering Task Force (IETF)’s OWE standard defined in RFC 8110.
OWE uses a Diffie-Hellman key exchange during the Wi-Fi authentication between device and Access Point (AP). This exchange sets up encryption without using a shared and public PSK (aka password).
The time to market for OWE is immediate with software (code) revisions.
RSNE
In 802.11 (Wi-Fi), APs use Management frames called Beacons to chirp/advertise information about a wireless network.
These Beacon frames carry various Information Elements (IE or IEs). One of them is the robust security network (RSN) element (RSNE). It’s identifier or type number is 48.
RSNE contains information about how a device can associate and connect to a secured Wi-Fi network (RSNE was introduced with the 802.11i amendment). Using this information, we can determine how a network is encrypted.
It’s important to note that the RSNE also carries associated subfields. So, we must look for the RSNE IE, and then look for specific subfields contained inside the RSNE. The one we’re looking for is the Authentication Key Management (AKM) suite. It also carries associated subfields which are a series of AKM suite selectors. These selectors identify what authentication types are used, like the ones for WPA2 or 802.1X. We can use these AKM suite selectors to determine if the network claims to support OWE.
OWE will show up as AKM suite type 18. You can discover this for yourself by looking at a pcap of a OWE enabled Network with Wireshark and inspecting the 802.11 dissectors, or with other protocol analyzers like Wi-Fi Explorer (macOS).
Here’s what the raw RSNE IE data looks like:
01 00 00 0F AC 04 01 00 00 0F AC 04 | 01 00 00 0F AC 12 E8 00 00 00 00 0F AC 06
Table 1:
| Octet: | Version | Group Data Cipher Suite | Suite Type | Pairwise Cipher Suite Count | Pairwise Cipher Suite List | Suite Type |
|---|---|---|---|---|---|---|
| HEX: | 01 00 | 00 0F AC | 04 | 01 00 | 00 0F AC | 04 |
| Decoded: | 1 | 00 0F AC | CCMP-128 (AES) | 1 | 00 0F AC | CCMP-128 (AES) |
Table 2:
| Octet: | AKM Suite Count | AKM Suite List | Suite Type | RSN Capabilities | PMKID Count | Group Management Cipher Suite | Suite Type |
|---|---|---|---|---|---|---|---|
| HEX: | 01 00 | 00 0F AC | 12 | E8 00 | 00 00 | 00 0F AC | 06 |
| Decoded: | 1 | 00 0F AC | 18 | N/A | 0 | 00 0F AC | BIP-CMAC-128 |
Here’s an example of deciphering the IE from a lightweight protocol analyzer I’m working on.
Version: 1, Group: 00:0f:ac AES, Pairwise: AES, AKM: OWE
Here’s what it could look like decoded in scan output:
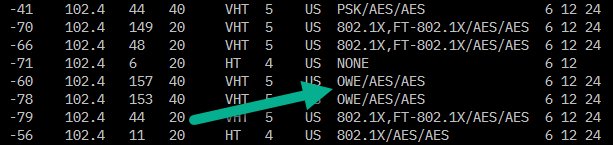
You can find out more about how the RSNE works by looking at the IEEE 802.11-2016 standard section 9.4.2.25 RSNE.
Change log
- 2019/02/18: spelling, minor changes
- 2019/02/19: clarification, added table
Thanks to Jacob Ingalls for reading drafts of this.
-
OWE does not perform authentication. It only provides does encryption. OWE also doesn’t protect against Man-in-The-Middle attacks that might lure your device to connect to a rogue AP, but it does protect against passive eavesdropping. ↩ ↩2
-
Layer 2 is the 802.11 data-link layer of the OSI model. This layer handles moving data in and out of the physical link (radio waves in this case). ↩
-
Substitute coffee shop for bar/pub, restaurant, gym, airport, hotel, your favorite retail store, home (where you should minimally use WPA2-Personal with AES/CCMP so that you can use 11n/ac (HT/VHT) rates); so, this is wherever you use an Open Wi-Fi network. ↩
-
Examples include Virtual Private Network (VPN) solutions, HTTP over SSL (HTTPS), Secure FTP (SFTP), Secure Socket Shell (SSH) as an alternative to Telnet, and many more. Note that HTTP, FTP, and Telnet were first designed without considering encryption. In the beginning, trust was assumed. ↩